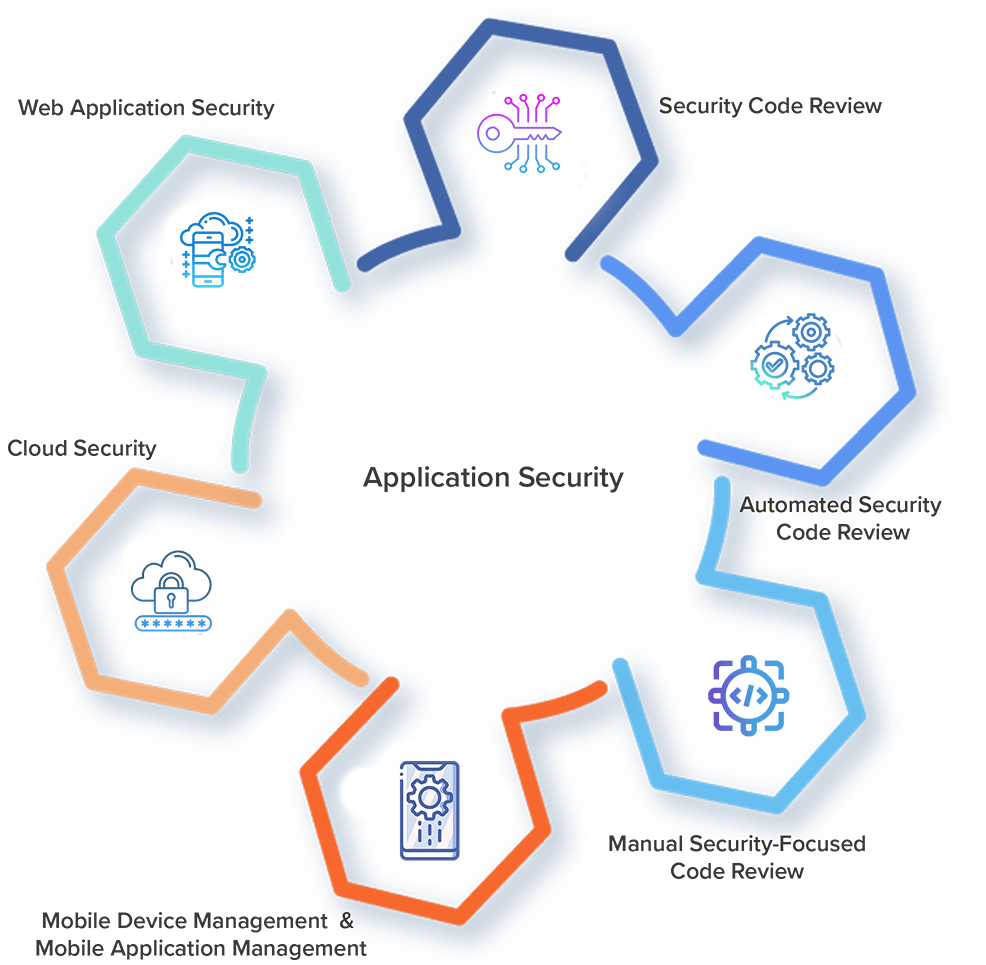
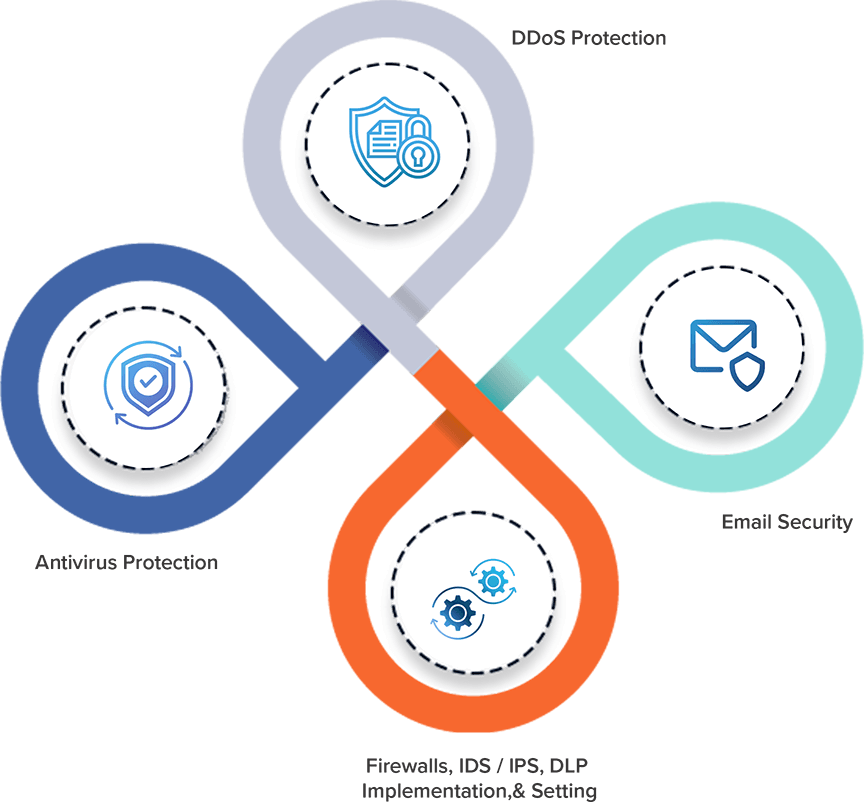
Jeanmartin’s security experts ensure proper protection of a website, a web app, or web services.
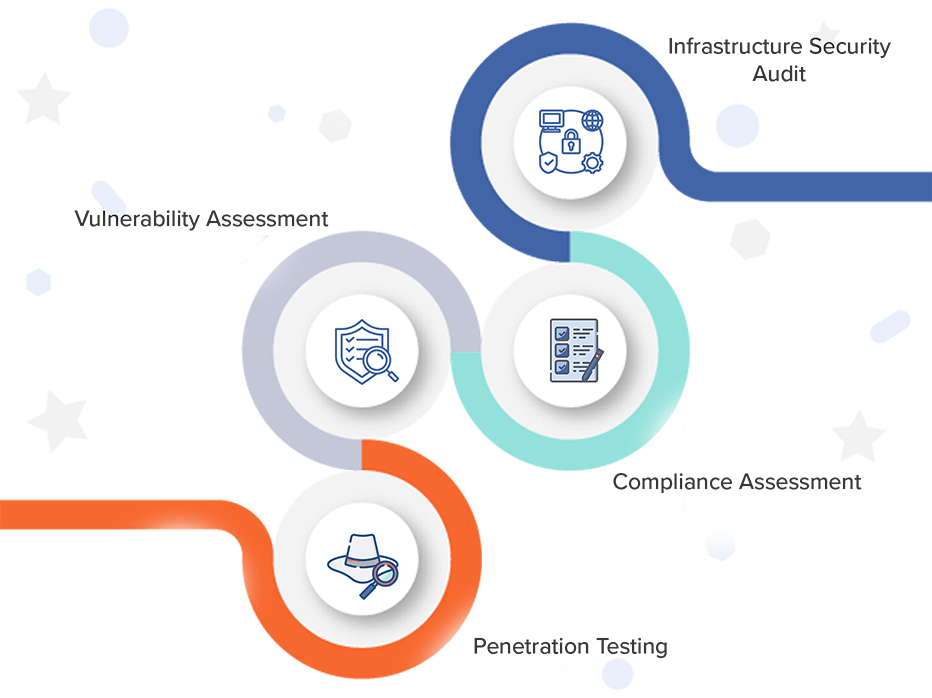
Our security testing team carries out vulnerability assessment to check whether the proper encryption, authentication and other security measures are applied in a web app, a web service or a website.
Upon the evaluation results, our security engineers provide customers with valuable recommendations on how to improve the protection level of their web solutions.
We offer penetration testing services (as a one-time or a regular service) to provide customers with detailed information on real security threats they may face and identify the most critical security weaknesses to let our customers prioritize remediation measures and apply necessary security patches.